What is Exposure Management and How Does it Differ from ASM?
https://firewall.firm.in/wp-content/uploads/2024/03/in.jpg
Startups and scales-ups are often cloud-first organizations and rarely have sprawling legacy on-prem environments. Likewise, knowing the agility and flexibility that cloud environments provide, the mid-market is predominantly running in a hybrid state, partly in the cloud but with some on-prem assets.
While there has been a bit of a backswing against the pricing and lock-in presented when using cloud infrastructure, cloud is still the preferred provider for the majority of SMBs.
As a result, external attack surfaces are increasingly complex and distributed and, therefore, harder to monitor and secure. This expanded attack surface gives hackers plenty of blind spots and gaps to exploit. Security teams are on the back, reacting, often too slowly, to changes in their own attack surface as engineering teams continuously spin up and expose new systems, services, and data to the internet.
This is compounded by the fact that the threat landscape is always changing. Thousands of new vulnerabilities are discovered every month, including vulnerabilities that allow an attacker to gain total control over systems that have to be internet-facing and are meant to support security teams or facilitate secure connections (take the spate of Citrix and Ivanti vulnerabilities that have recently emerged). How can you react to a new critical vulnerability that’s being exploited by ransomware gangs if you don’t even know if your organization is using that technology and exposing it to the internet?
One of the reasons that security teams struggle is because processes are reactive and knowledge about the organization’s attack surface is siloed in the heads of those people who are spinning up those cloud systems. Security teams rely on a sprawl of solutions that generate loads of fragmented data that’s difficult to understand, prioritize, and take action. This is where exposure management fits in as an extension of external attack surface management.
What is exposure management in cybersecurity?
As environments evolve and become more complex, so do the tools and techniques needed to secure and protect them. Exposure management aims to reduce that complexity by giving you visibility of all points within your attack surface that an attacker could use to breach your organization and ultimately pose a risk to the business.
Exposure management aims to provide a prioritized list of exposures, with context for each so that you can make an informed decision on what to tackle first and how to tackle it to reduce your business risk.
“Organizations who implement a continuous exposure management program will be three times less likely to be breached by 2026” (Gartner)
Exposure management can also help increase visibility of your entire attack surface, including data assets such as code repositories like GitHub and GitLab, so you can more accurately find opportunities for an attacker and shut them down before they pose too great of a risk to your business.
This means you can better understand the risks you face, and prioritize the attacks that are not just more likely, but more serious. At a time when security teams are overwhelmed with data – over 25,000 vulnerabilities were published in 2022, and we saw that increase to over 26,500 in 2023 – having a clear picture of where to focus your time and effort is becoming essential.
Exposure management vs attack surface management
While both have the same goal, there are important differences between the two. External Attack Surface Management (ASM) is the ongoing process of discovering and identifying assets which can be seen by an attacker on the internet, showing where security gaps exist, where they can be used to perform an attack, and where defenses are strong enough to repel an attack. If you can scan for it using vulnerability scanning then it generally falls within attack surface management.
Exposure management takes this a step further to include data assets, user identities, and cloud account configuration, which helps you understand your exposure and reduce it where necessary.
Here the attack surface includes any of the SaaS products you use. If one of these gets compromised or one of your accounts in your SaaS provider gets compromised, they have information that can be used to facilitate other attacks. So it shouldn’t be forgotten when assessing risk to the business.
Visualize and minimize your exposure with Intruder
Remember what was said about a large attack surface being harder to defend? You can reduce yours by continuously monitoring for changes with an automated vulnerability management tool like Intruder. Get complete control of your vulnerability management to:
- Discover assets: when new cloud services are spun up and exposed to the internet, Intruder will kick off a scan to find any vulnerabilities so you can fix them faster
- Know what’s exposed: get complete visibility of your network perimeter, track active and unresponsive targets, identify changes, monitor expiring certificates, and see any ports, services or protocols that shouldn’t be exposed to the internet
- Detect more: Intruder uses multiple scanners to identify vulnerabilities and exposures across your attack surface giving you the greatest visibility
- Focus on the big issues: get results prioritized based on context, so you can focus on the most pressing problems without wasting time sifting through the noise
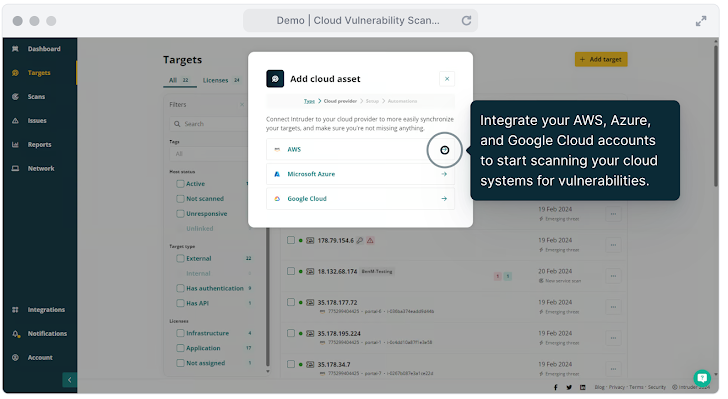 |
| Intruder continuously monitors and automatically scans your environments as new vulnerabilities emerge |
Premium and Vanguard customers can also boost their exposure management with bug hunting, where Intruder’s testers look for the weaknesses and exposures that automated scanners can miss. Get started with a 14-day free trial today.
 Firewall Security Company India Complete Firewall Security Solutions Provider Company in India
Firewall Security Company India Complete Firewall Security Solutions Provider Company in India











